With more and more businesses switching over to the cloud, it is imperative that companies move beyond standard security measures to adopt solutions like CASB. Cloud security is more than just blocking unwanted content. With CASB, businesses can gain greater visibility into user data, assess the risks of using various cloud services, and protect sensitive information from hackers.
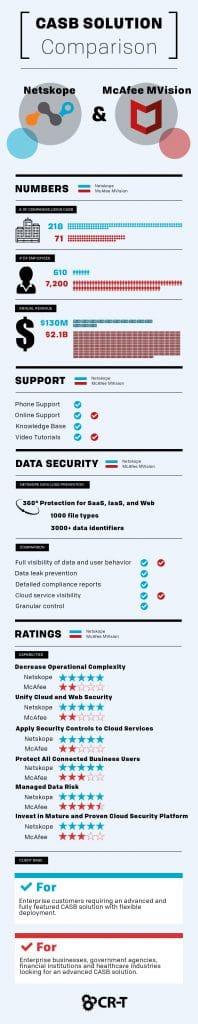
A Cloud Access Security broker (CASB) is a security policy enforcer that acts as a go-between for consumers and cloud service providers. Available either on-premise or in the cloud, CASB provides security beyond the application itself. CASB examines risks, enforces policies, and complies with regulations. Netskope is one of the leading CASB platforms.
According to Netskope, cloud services account for 85% of all enterprise web traffic. With so many cloud services to manage, it is becoming more critical than ever for companies to take advantage of CASB.
Gartner predicts that 85% of large enterprises will use a CASB platform for their cloud services by 2020. With a variety of capabilities to choose from, CASB can help you take your business to the next level.
Multi-Mode CASB Operation
Businesses generally choose either proxy-based or API-based CASB solutions, depending on their needs. Most businesses consider API to be a newer and more sophisticated approach to CASB. However, utilizing a multi-mode CASB operation is also becoming popular, as it supports both proxy and API modes.
Proxy-Based CASB
Proxy-based CASB is an in-line solution that filters traffic through a gateway, checking users and devices as they pass through.
With a reverse proxy deployment mode, the cloud service routes traffic directly to the CASB proxy, reducing the overall amount of traffic. A forward proxy deployment mode creates an “SSL man-in-the-middle” system, where a device or network routes traffic to the proxy.
Since it uses only a single checkpoint, proxy deployment offers real-time security, which leads to faster detection. However, the single checkpoint also means that proxy mode can affect the network performance. Additionally, proxy-based CASB is only configured to secure SaaS cloud services, leaving IaaS and PaaS unprotected.
API-Based CASB
API mode is an out-of-band deployment mode that integrates with the cloud application to access the application directly, without needing to use a gateway.
API offers fully-comprehensive protection and universal coverage, including both north-south (user-to-cloud) traffic and east-west (cloud-to-cloud) traffic. The biggest downside of API deployment is its limited real-time policy enforcement, meaning that it can be several minutes before an issue is detected.
Multimode CASB
Some platforms, like Netskope, offer advanced APIs with faster response times. However, you can enjoy the benefits of both API and proxy modes by choosing a multi-mode option.
Perhaps the greatest benefit of multimode CASB is that it gives customers a wider range of choices. Netskope offers multimode solutions for cloud-native data security. With such a wide variety of security options to choose from, you never have to settle when you choose Netskope.

CASB Shadow IT Visibility
Cloud usage among businesses is only growing in recent years. A 2018 Netskope report showed increased adoption of the public cloud. And with a growing number of cloud services, the amount of shadow IT that companies have to deal with is also increasing.
CASB can help businesses discover and manage shadow IT. This ultimately reduces costs and increases productivity.
Shadow IT includes all IT-related activities that are handled outside of the IT department. Cloud services, like SaaS have become the most prevalent form of shadow IT. While these tools offer greater ease of use and efficiency, they also harbor security gaps that create risks for businesses.
In fact, Netskope has revealed that companies, on average, have 1,295 apps and cloud services, with less than 2% managed by IT administration.
While eliminating the use of cloud applications is often impractical, businesses can use cloud services responsibly and stay prepared to respond to potential risks. CASB offers greater visibility into shadow IT, which can reduce many of these security gaps.
How to Manage Shadow IT Risks
In order to combat shadow IT risks, companies must first learn the extent of shadow IT within their organization. This can be accomplished through a CASB platform or a personalized assessment, like Netskope’s Cloud Confidence Audit. Many CASB solutions also make it possible to assess cloud service risk by providing a risk score.
After determining the effect of shadow IT on an organization, you can choose to apply specific cloud governance policies and obtain deeper visibility into user activity.
Netskope offers Shadow IT and Unmanaged Cloud Protection. With Netskope, you can gain full visibility of your cloud services and assess the risk of each of these services. Identifying accurate cloud usage then allows you to consolidate any redundant data. Netskope also offers a Cloud Confidence Index (CCI), giving you the ability to learn about vulnerabilities within an app.
CASB Data Security
Cybersecurity is one of the main focuses in the modern business world. Verizon estimates that 58% of data breach victims are small businesses. Additionally, IBM claims that the average cost of a data breach is $3.86 million.
With so much data being stored in the cloud, it is essential for businesses to have some form of data security in place. CASB offers a variety of data loss prevention options, from cloud encryption to IRM. Invest in a CASB solution that will help you protect sensitive information and leave your data secure.
According to Netskope, increasing your number of cloud apps by 25% over the course of a year would increase your chances of a data breach by 75%. To protect you from cyber attacks, Netskope offers data loss prevention through the Netskope Security Cloud. This service offers you greater visibility and real-time data and threat protection.
Cloud Encryption
One way to protect data from unauthorized access is cloud encryption. After transforming plain text into cipher text, the data becomes unreadable for anyone without the encryption key(s). This method also allows for multiple levels of protection.
With symmetric key encryption, the same key is used to both encrypt and decrypt data. This makes it easy to access and alter data, but it also leaves data vulnerable to third parties who have the key.
An even more secure method is asymmetric key encryption, which uses two different keys—one for encryption and one for decryption. Companies can safely exchange data with third parties, while still keeping the data protected.
Netskope offers a variety of encryption options so that you can find the right solution for your business.

Tokenization
Another data security option is tokenization. Similar to encryption, this method creates a token value for the plain text, restricting data access.
However, tokenization doesn’t use a key to decrypt the data; instead, a separate database called a token vault stores the relationship between the sensitive information and the token. With no mathematical relationship to the data, it becomes a lot more difficult for outsiders to access the secured information.
Information Rights Management
Information rights management (IRM) encrypts files and then applies IRM rules in order to protect sensitive documents from unauthorized access. These custom rules can be developed at the enterprise level, department level, group level, or user level. The protections that are created will remain, even when the file is shared with third parties.
Netskope allows you to gain complete visibility into data so you can easily manage sharing permissions and access control. Whether you choose encryption, tokenization, or IRM, CASB will keep your data secure, while still giving you the ability to share information with third parties.
CASB Threat Protection
Every day, your business’s network is susceptible to cyber attacks from outside threats.
According to the University of Maryland, a cyber attack occurs every 39 seconds. And Small Business Trends estimates that 43% of these attacks target small businesses. Implementing CASB can provide your business with greater protection so that you can better prevent and respond to cyber attacks.
One way that CASB can protect your network is through account management and security. With account takeover protection, CASB uses machine learning to prevent accounts from becoming compromised. You can create rules for screen access and implement multi-factor authentication to protect accounts from unauthorized access.
According to the Verizon 2015 Data Breach Investigations Report, five malware events occur every second. Malware can enter a device through file sharing, browser extensions, and applications.
CASB can detect malware by comparing various user patterns in order to identify unusual behavior. Netskope uses prediction capabilities to understand how users interact with cloud service providers. Going beyond basic rule-setting, Netskope can thoroughly differentiate user behavior from machines behavior in order to prevent attacks.
A Customer-Centric Approach to CASB
Regardless of your position or the size of your company, you deserve a CASB solution that is catered to your needs. CASB platforms like Netskope will provide you with the visibility and security you need to build a more stable network. Contact us for a free consultation, and we will help you get the support you need.
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure, to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of




