With the upcoming release of The Rise of Skywalker this weekend, Star Wars fans are abuzz with predictions, theories, and analyses of past movies. Everyone is waiting, with bated breath, to see how the Resistance will fare in the final battle against the First Order. Remarkably, both the Resistance and the original trilogy’s Rebel Alliance have experienced great degrees of success against their enemies, despite having smaller forces and significantly less resources. What inspired these victories, and how were these smaller groups able to consistently come out on top?
First, it is important to note that throughout the Star Wars saga, the Empire had all of the tools necessary to succeed. They outranked the Rebel Alliance in resources, manpower, and weaponry. Although smaller than the Empire, the First Order had many of these same advantages.
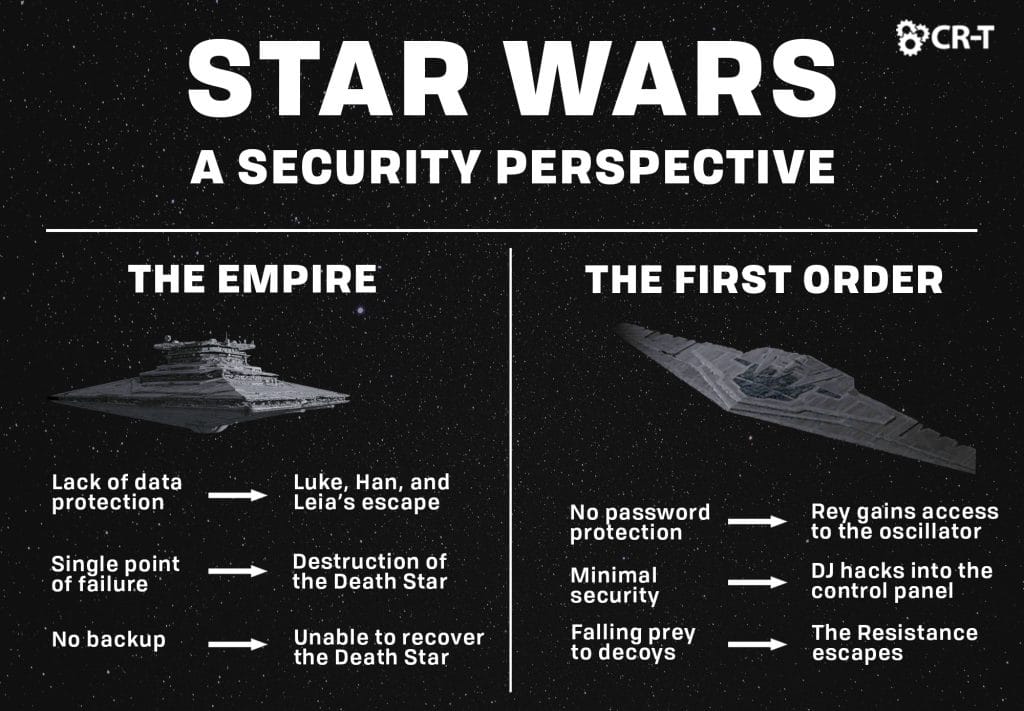
The problem with both groups is their weakness in security. Despite building powerful battle stations and maintaining significant control throughout the galaxy, both the Empire and the First Order failed to implement basic security measures, like access control, encryption, data loss prevention, employee training, backup, and disaster recovery technology and policies like Unitrends.
These security failures are what led to the fall of the Empire and what allowed the Resistance to escape in Star Wars: The Last Jedi.
Star Wars: The Empire
The Empire struggled with security from the beginning. In Star Wars: A New Hope, the lack of data protection was astonishing. Following Princess Leia’s capture, R2D2 was easily able to plug into the Empire’s network and find the location to her cell.
In other parts of the film, R2 retrieved information regarding the Death Star’s tractor beam. He also manipulated a trash compactor to save Han, Luke, and Leia. The fact that R2 never encountered a firewall or any form of password protection means that any person aboard the Death Star could easily access the network and retrieve top-secret information.
A Single Point of Failure
Additionally, none of the Empire’s systems or data were encrypted or backed up in any way. When the Rebels gained access to the Death Star plans, they were immediately able to interpret the information and develop a plan of attack.
In the Battle of Yavin, the Rebels targeted a single point of failure in the thermal exhaust port. This allowed them to destroy the Death Star by simply debilitating the port. The security issue lies not only in the weakness of a single point of failure, but also in the fact that the Empire failed to provide any sort of backup for the port. Once the port was destroyed, the entire Death Star collapsed.
The Empire experienced many of the same problems when defending Death Star II. The Rebels launched a two-pronged attack. A ground force attempted to destroy the shield generator on the planet Endor. Meanwhile, the Alliance fleet attacked from space, waiting for the shield to go down before targeting the reactor core of Death Star II.
The Death Star was ultimately destroyed when the Rebel ships shot directly at the reactor core without any internal intrusion detection systems. Again, the battle station contained a single point of failure and lacked the necessary backups to function in case of an emergency. Like the previous Death Star, Death Star II was left vulnerable, making it easier to destroy.
Countless Security Flaws
There were several reasons for the Empire’s failure, but ultimately, they lacked the necessary security to defend themselves.
There were no basic measures like access control and encryption on the Empire’s ships. Without this security, the Rebels were easily able to discover secure information, like the location of high-security prisoners and the blueprints for the Death Star.
Additionally, the lack of an intrusion detection system on the Death Star made it easy for the Rebels to get within range and exploit the ship’s weaknesses.
Finally, there was no backup support on either Death Star, so targeting a small area ensured the destruction of the battle station.

Star Wars: The First Order
Built from the ashes of the Empire, the First Order was a military superpower—albeit much smaller than the Empire—that sought to take over the galaxy.
Following the Galactic Civil War, the New Republic passed the Military Disarmament Act. This significantly reduced the size of the Republic’s centralized military. Leia formed the Resistance to act as a private military force, but she was unable to receive much assistance from the Republic. The Republic was destroyed in Star Wars: The Force Awakens, when General Armitage Hux used Starkiller Base to destroy the Hosnian system.
Employee Access to Crucial Information
After learning of Starkiller’s existence, the Resistance made a plan to destroy the weapon. Finn recreated blueprints from information he had been given access to. He gave these to the Resistance, and they discovered a thermal oscillator that powered the weapon. By tracking one of their captured fighters, the Resistance was able to locate the planet. Han, Chewbacca, and Finn snuck onto the base and captured Captain Phasma, ordering her to lower the shields before throwing her in a garbage chute.
Like the Empire, the First Order seems to have fallen victim to many of the same security weaknesses. The fact that Finn was able to access top-secret information while working as a janitor is startling. However, so is Phasma’s immediate willingness to compromise the security of the entire base.
Lack of Password Protection
While on the base, Rey was able to open a doorway to the oscillator, allowing Han and Chewie to plant a series of thermal detonators from within. Once the explosives created an opening, Poe flew directly into the oscillator and fired, destroying it and causing a chain reaction.
This attack could have been prevented had the First Order employed greater security. Some form of access control or password protection would have prevented Rey from opening the hatch and allowing Han and Chewie to plant the explosives.
Additionally, the fatal flaw of each Death Star—both the two created by the Empire, and Starkiller base—was a single point of failure that immediately caused the destruction of the entire battle station. After witnessing the Empire’s failure, the First Order should have provided greater security for the oscillator, as well as created a backup in the case of the oscillator’s failure.
Falling Prey to a Decoy
Following the Battle of Starkiller Base, the Resistance prepared to evacuate their main base. Meanwhile, Poe confronted the First Order fleet in his X-wing, acting as a decoy to lure out the Dreadnought Fulminatrix.
Although they suffered devastating losses, a squadron of Resistance bombers were able to destroy the Dreadnought. By falling prey to Poe’s decoy, the First Order lost a magnificent ship and failed to overtake the Resistance before their evacuation.
Insufficient Protection Against Hackers
Despite this initial loss, the First Order tracked the Resistance through hyperspace, causing the Resistance fighters to quickly become desperate for a plan.
After Leia became incapacitated, Vice Admiral Amilyn Holdo took charge of the Resistance. Finn and Rose snuck away and embarked on a secret mission to Canto Bight. There, they found a master codebreaker who they believed could help them remove the First Order’s hyperspace tracker. However, they were captured before they could approach the codebreaker. Instead, they reluctantly enlisted the help of slicer DJ.
After stealing a ship, DJ was able to cloak their entrance onto the First Order’s ship, the Supremacy. He then sliced into the control panel using Rose’s Haysian smelt necklace. The First order doesn’t initially notice Rose, Finn, and DJ entering the Supremacy. Were BB8 not with them, they might have been able to escape the ship without being detected. The ease with which DJ was able to hack into the control panel also suggests a need for added security.
Additional Decoys
Onboard the Raddus, Vice Admiral Holdo prepared an evacuation to the nearby planet Crait via a fleet of U-55 orbital loadlifters. Holdo remained on the Raddus as a decoy, while the Resistance slipped away, undetected. The First Order didn’t initially notice the loadlifters, due to their small size. It wasn’t until DJ alerted them that the First Order was able to launch an attack on the much smaller Resistance ships. After landing on Crait, the Resistance was then able to escape by using another decoy, Luke Skywalker.
The First Order’s pride and inability to detect these threats is what led to their failure.
These examples make it clear that a lack of security can have devastating consequences, especially when relying on old techniques that have been exploited in the past.
The First Order was unable to learn from the mistakes of the Empire, and as such, the Resistance easily infiltrated their system and destroyed Starkiller Base.
Additionally, the Resistance was innovative enough to implement a decoy strategy multiple times, which is ultimately what allowed them to escape in The Last Jedi.

Star Wars: An IT Application
Employee Risk
One of the greatest risks to any business is its employees. In the Star Wars saga, we see many instances in which storm troopers became a point of failure for the Empire.
On multiple occasions, Jedi were able to overpower storm troopers using the force. This allowed them to access critical information and escape from otherwise secure locations.
In The Force Awakens, Finn recreated blueprints from the First Order and delivered them to the Resistance. Later, Finn, Han and Chewie threatened Phasma into lowering the shields of the Starkiller planet. Many of these situations could have been avoided with proper employee training.
Throughout the Star Wars movies, it is painfully obvious that members of both the Empire and the First Order are unsure of what to do during a security breach.
Similarly, untrained office employees, when faced with a security breach, often become deer in the headlights, with no idea of how to respond.
By properly training your employees, you can help them prevent security breaches and learn how to respond when attacks occur.
Data Loss
Additionally, both the Empire and the First Order have a history of data loss. Important information—like the location of high-security prisoners and access to battle station blueprints—was easily accessible to anyone aboard the ship. Infiltrators, like the rebels, or even low-level employees, like Finn, were able to steal important data. This made it much easier for the opposing side to take advantage of structural weaknesses.
In a business, leaving your data unprotected makes a data breach almost inevitable. Secure your data with the proper authentication and passwords. Only give data access to employees to relevant employees who need the data in order to perform their jobs. When employees leave the company, make sure their access is removed, and erase any company files from their devices.
Backup, Disaster, and Recovery
Finally, have a plan in place in case you fall victim to a security breach. Back up important data and systems in a secure location. Have an incident response plan (IRP) that is regularly reviewed and updated. Make sure your employees know what to do in the event of an attack. Most problems can be avoided through careful preparation.
Stay Protected
Security can be difficult for a company to manage, especially with the advanced techniques that cybercriminals use. Our team of experienced professionals can help you find the best security options for your business, from spam protection, to backup and disaster recovery.
A lack of security caused the Empire’s downfall, and the First Order is currently heading down that path. Don’t make the same mistakes. Invest in your business by making security a priority.
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure, to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of





