When you go to the hospital to have your appendix removed, you don’t expect your identity to be stolen as well. But like any other corporation, the healthcare industry isn’t immune when it comes to cyber attacks. In fact, attacks on healthcare facilities can have even more devastating consequences than the average security breach.
Let’s talk about some of the most common attacks against the healthcare industry, along with how to combat these attacks.
Why Healthcare Organizations are Easy Targets for Cyber Attacks
As a whole, the black market value of health records is decreasing when compared to assets like credit cards or social security numbers. But medical information is still considered to be one of the most profitable rewards for cyber criminals.
And healthcare-targeted cyber attacks are among the most dangerous, sometimes becoming a matter of life and death.
For example, what if someone hacked into your pacemaker or insulin pump? Such an attack could have devastating consequences.
Unsecured Endpoints and Devices
Hospitals are filled with a variety of connected devices which presents a host of security challenges. Modern IoT devices like wearable monitors often operate on the same network as older, less secure devices.
This gives criminals plenty of opportunities for infiltrating sensitive networks to spread viruses or steal information.
Even something as standard as a Windows computer can create a security risk if the operating systems aren’t kept up to date. Many hospitals are still using Windows 7 and Windows XP platforms, which are twice as likely to become infected than a Windows 10 operating system (source: Webroot).
Disjointed Operational Structure
The size and complexity of a hospital environment can also lead to security vulnerabilities. Hospitals often contain multiple buildings, each with their own units, wards, and offices.
With so much data being shared across the network, there’s not a lot of room for error. And coordinating security measures between different institutions is often a slow and challenging process. This makes it a lot easier for security gaps to arise, and it can lead to larger problems down the road.
Opportunity to Steal Valuable Research
In addition to their complexity, medical institutions often contain important data, such as groundbreaking research. This research may take decades and millions of dollars to develop, but it can be stolen in a matter of minutes.
Some criminals steal research in order to outpace competitors, while others will try to ransom the research or sell it for a profit.
Greater Likelihood of Receiving a Ransom
Cyber attacks are especially disastrous for hospitals since downtime can affect patient care and even risk lives.
This makes healthcare facilities an easy target for cyber criminals. If a hospital is hit with a ransomware attack, they usually have no choice but to pay the ransom.
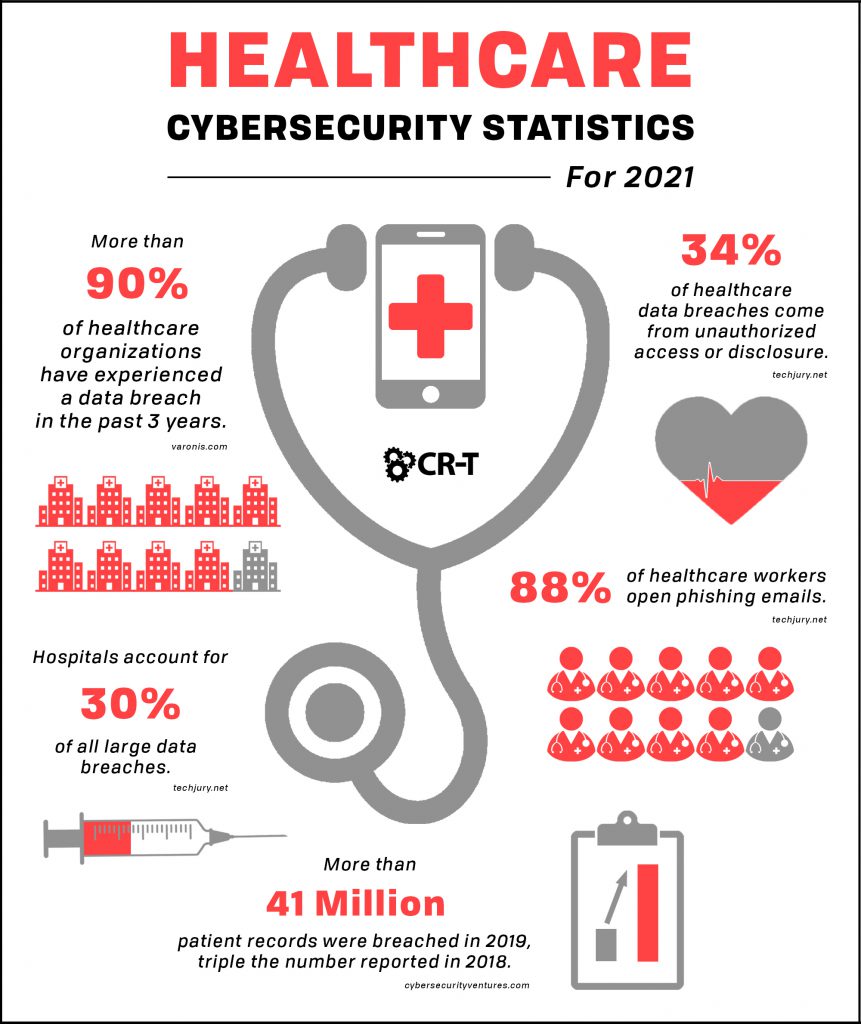
Most Common Attacks
We’ve discussed a few potential reasons that cybercriminals may target the health industry.
Now, let’s take a look at some of the most common attacks and why they’re so profitable for hackers.
Attacks on Imaging
Outdated imaging equipment is an easy target for hackers. These systems are often used beyond their life expectancy, and they rely on obsolete operating systems like Windows NT and XP.
Legacy imaging equipment serves as a “pivot point” for cyber criminals, allowing them to gain access to medical information and other technology systems. Even outdated malware can successfully infiltrate a legacy system.
Medjacking
Another frequent form of attack is “medjacking,” or the practice of hacking a medical device with the intent to threaten or harm a patient.
Vulnerable devices include PET and CT scanners, pacemakers, infusion pumps, medical lasers, ventilators, and dialysis machines. These devices are made vulnerable by their outdated operating systems, making them easier to hack.
Once patient records are stolen, they can be sold on the black market or encrypted and held for ransom. If the records aren’t recovered in a timely manner, the patient’s life could be at stake.
Enterprise Vulnerabilities
In addition to attacking individual devices, attacks on healthcare enterprises as a whole are becoming more common.
For example, if a patient logs into their patient portal while on a public network, another person on the network would have no trouble hacking into their account and accessing their records.
And anyone hacking the public network, regardless of their physical location, could plant malware capable of invading all connected IT systems.
Ransomware
Ransomware is one of the most common cyber attacks targeted at healthcare facilities.
Instead of simply stealing data, cyber criminals will encrypt patient records and then demand payment in exchange for their decryption.
Many hospitals will pay the ransom out of desperation, but even then, there is no guarantee that the hacker will unlock the computer or decrypt the files.
Phishing Attacks
But how exactly do criminals get a hold of sensitive data in the first place?
If a hacker can successfully trick an employee using a phishing attack, they can then use the employee’s account or device as a backdoor entrance into the entire network.
Phishing attacks usually appear in the form of an email that might seem legitimate but contains a dangerous link or download. Following the link could infect the computer with a virus or give criminals access to the network.
Strategies for Improving Cybersecurity in the Healthcare Industry
So how can healthcare workers and institutions better prevent and mitigate the damages of a cyber attack?
While there isn’t a surefire way to protect patient data, there are a lot of preventative measures that physicians can take to improve security.
Here are a few steps hospitals and other healthcare facilities can follow in order to improve their security:
- Establish a security culture. Regularly train employees on the importance of cybersecurity and emphasize every team member’s responsibility for protecting patient data and creating a culture of security.
- Protect mobile devices. An increasing number of healthcare workers are using mobile devices while on the job. Ensure that these mobile devices are encrypted and connected to secure networks.
- Practice smart computer habits. New employees should be trained on best practices for computer use, including learning how to recognize phishing emails and how to maintain software and operating systems.
- Install firewalls and antivirus protection. Firewalls and antivirus software will help you monitor your network and scan for suspicious activity. It’s also important to keep your antivirus software up to date so your systems receive the best possible protection.
- Control access to sensitive information. Computers should be password-protected and kept locked when not in use. Healthcare organizations should also limit access to sensitive health information. Higher-level accounts can be further secured with methods like multi-factor authentication.
- Create a response plan to mitigate the effects of a cyber attack. Regularly back up your files to allow for quick and easy data restoration. Establish security measures that will allow you to quickly identify and neutralize attacks.
- Have a plan in place for recovering from a cyber attack. Establish what information has been compromised, and reach out to any affected parties. Perform a total security update to ensure that no other devices were infected.
In addition to conducting your own cybersecurity audits, it can be helpful to get a fresh perspective. IT professionals are trained on the ins and outs of cybersecurity, and they can help you identify any gaps and better protect your patients and their data.
Keep Your Patients’ Information Protected With Strong Cybersecurity
Strengthening your cybersecurity will not only benefit your institution, but the lives of your patients as well.
Our cybersecurity experts can help by auditing your current security systems and offering guidance on how to improve your cybersecurity.
Don’t wait until a patient’s life is on the line. Learn how to better protect your organization by scheduling a free consultation today.
Here at CR-T, we take pride in providing enterprise-level IT services at prices that work for small businesses. Our team of experts can become your IT support department, responding to issues quickly, often before you even know about them. Covering everything from your servers and network infrastructure to your computers, workstations and mobile devices, we provide end-to-end solutions for all your technology needs.
Time and experience have helped us develop best practices and workflow procedures designed to keep your focus on your business, not your technology.
Blog & Media
Cloud Services
Managed IT Support
Cyber Security
Project Services
Servers/Infrastructure
Firewalls
Networking
Hardware/Software
Microsoft Products/Cloud
Amazon Web Services
Penetration Testing vs Vulnerability Scanning
If you’re responsible for managing the security of your organization’s network or systems, you may have heard the terms “penetration testing” and “vulnerability testing” thrown
Backup and Disaster Recovery
Your organization can’t afford to neglect backup and disaster recovery. If it takes your business too long to get back online after a disaster, you
6 Steps to Secure Customer Data
Securing customer data is essential for one major reason: your business depends on it. As an IT director, you recognize the importance of cybersecurity when
5 Steps to Promote Compliance in the Workplace
You’re familiar with the ever-changing world of regulatory compliance. Robust compliance enables you to avoid legal liabilities while improving your organization’s effectiveness. And many of






